
Are you getting emails with subject line like this one: “Your iCloud Account Will Be Closed – on 02/05/2025”,? The content of the email have usually an urgent tone requesting you to take action as soon as possible to resolve the issue. This action maybe a web link to click on or a phone number to call. Whenever action you take may caused you to get scammed or hacked.
This is a type of social engineering scam called phishing and its on the rise. A social engineering scam is a type of cyberattack where criminals manipulate people into revealing sensitive information, granting access to systems, or performing actions that benefit the scammer. Instead of hacking systems directly, attackers exploit human psychology—such as trust, fear, or urgency—to trick victims.
According the 2025 IBM Threat Intelligent Index, the number of infostealers delivered via phishing emails per week increases by 84%. Phishing has emerged as a shadow infection vector for valid account compromises. By clicking on links that seem legitimate, users can unknowingly open the door to infostealer malware that siphons sensitive data from victims. Because adversaries hide and deliver malware payloads more cleverly, it can take longer to detect ransomware and data breaches.
Common types of social engineering scams
Below are common types of social engineering scams you may encounter and some useful tips to avoid being a victim.
Phishing
Criminals use fraudulent emails, texts, or calls pretending to be from a trusted source (e.g., banks, tech support) to steal login details or money. In this case, the cyber criminals don’t have a specific target. They just reach out to people in general and wait for to see who is going to take the bait. You get it, it’s literally like fishing!
Fraudulent emails are the preferred method for these internet criminals. Emails can be sent to millions of people with only one click. Plus, it’s less expensive. Even though these emails seem to be coming from legitimate companies at first glance, it’s pretty easy to verify their credibility with a little observation of the email content.
If you received a suspicious emails, first of all, check the sender email address. The address will likely be not matching the company their impersonating. This is an example of a phishing email I received claiming to be coming from Apple iCloud service. When I revealed the sender email details, it’s coming from glitchtrap@make.phmdream.com. Needless to say this has nothing to do with Apple.
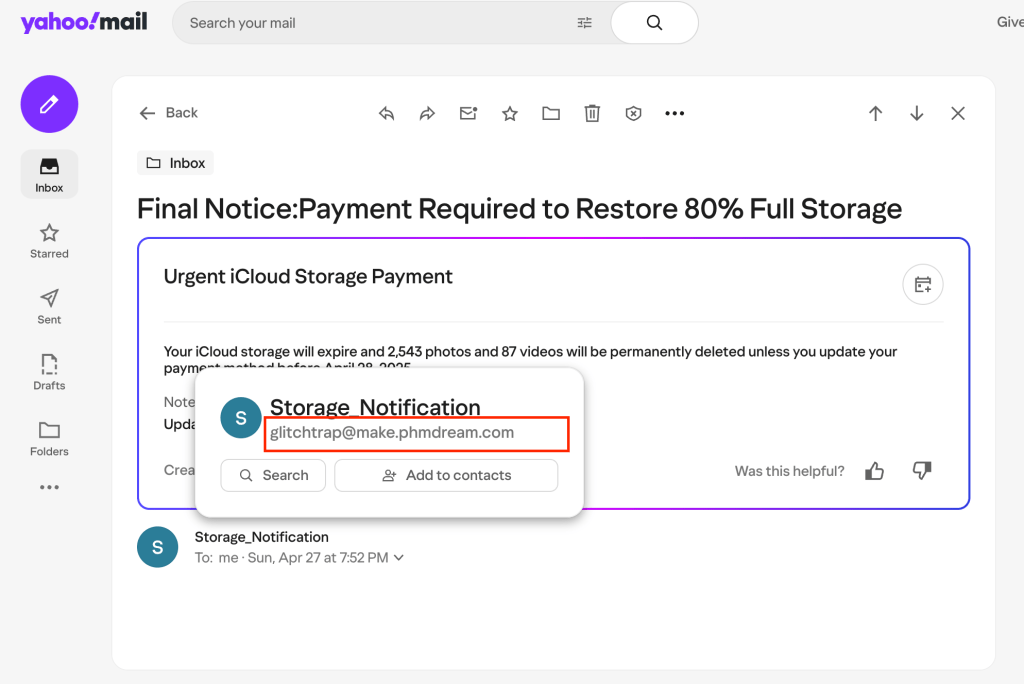
Second, look for a sense of urgency in the email content. Scammers play on human psychology to try to gain their potential victim trust. They use two big human emotions to achieve this: Fear or greed. Greed is use in the context of get you exited to received something. An opportunity to not missed. In fear, they make you feel like you are about to lose something you already have. In the email below, the scammer used dramatic and bold word to tel me I will permanently lose access to my iCloud. Notice they used a red text color to make sure I see this. It’s meant to create fear and panic.
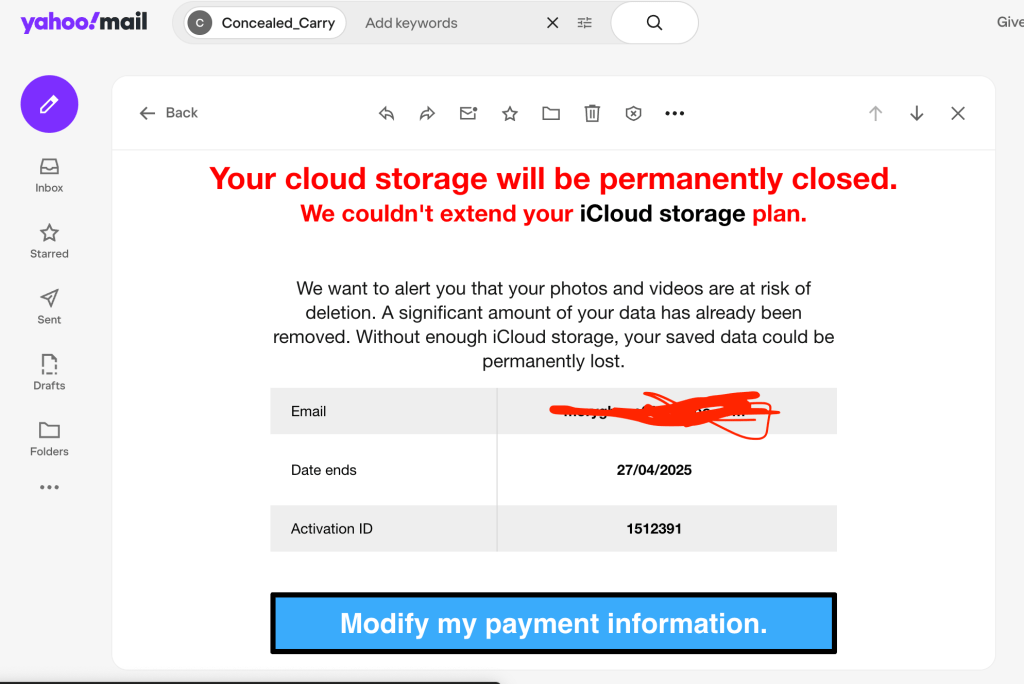
Lastly, there will always be CTA (Call To Action) at the end of the email content. In the above example, the big blue rectangle with the text “Modify my payment information” is a link the scammer provided. Sometime the CTA can be a number to call.
If you received an email and you couldn’t determine if it’s phishing email or not, it’s best to call search the official number of your company and found out more about the email.
Vishing (Voice Phishing)
Vishing is when scammers use phone calls instead of emails to target their potential victims. They pretend to be from tech support, banks, or government agencies to extract personal data.
I live in the U.S and I frequently received phone call from people trying to offer me a loans, government benefits, or even job offers. A good trick is to stay calm, listen to the person on the phone while using your critical thinking skills to see whether they manipulating you or not. If the call is about something you are not even interested in, you can just says “Thank you, but I’m not interested” and hang-up. If for some reason you are interested by what is being offer to you, then never disclose any personal information like full name, birth date, social security number, or address. If it’s a scam, it will have the same sense of urgency and request you to take a quick action as we saw in the emails phishing.
If you determined that the caller was a scammer, you can take further steps and block their contact so they don’t call you again from that number. If you own an iPhone, you can do this by going to the caller profile, and there will be a “Block Caller’ option at the very bottom of the setting. (see image below)

Smishing (SMS Phishing)
Smishing is a type of phishig where attackers use fraudulent text messages with malicious links or urgent requests (e.g., “Your package is delayed—click here!”). People tend to respond quick to an sms than an email, so smishing is becoming one the preferred method of social engineer criminals.
Like in the other cases, use critical thinking skills before you take any actions. Also remember, since this is a phishing, there will always a sense of urgency and a call to action in the sms content. You can also block that number to avoid being contacted again.
Impersonation Scams
According to CFO DIVE, Cybercriminals utilized AI deepfakes to falsely pose as Arup’s CFO and other employees, leading a staff member to transfer $25 million to Hong Kong bank accounts.
In impersonating scams, attackers pose as a CEO, coworker, or family member to trick victims into sending money or data. Their use powerful A.I tools to alter their voice or image to create manipulated videos, audio, or images that impersonate individuals, often for financial gain or to spread misinformation. These scams exploit the increasing sophistication of AI to create realistic content, making them difficult to detect.
If you are in a situation where you think someone is pretending to be a family member or a friend, try to not panic and use the same critical thinking skills to detect any sign of scam. Remember the most obvious will be a sense of urgent and requesting you to take quick action. If you are not to sure, it’s better to trick to caller that you will call them back so you can try to reach that relative directly or notify law enforcements.
Social engineering scams succeed because they exploit human emotions—fear, curiosity, or urgency. Staying cautious and verifying sources can prevent most attacks. While there are many other types of social engineering scams and I can’t cover them all here, below are some quick tips to protect yourself about most social engineering scams.
- Verify unexpected requests (call the official number to confirm).
- Never share passwords or financial details via email/phone.
- Check URLs & email addresses for inconsistencies.
- Enable multi-factor authentication (MFA) on accounts.
- Be skeptical of urgent/scare tactics (e.g., “Your account will be locked!”).
- Educate yourself & others about common scams.






Leave a comment